The Sounds of the Blue Mountains
The dominant sound in our beautiful city in a National Park especially in Hazelbrook today and almost every day is the roar of the chain-saw, the grinding of the chipper as yet more of our emblematic trees is reduced to chips. Bad luck for the possums, miniature bats, koalas and birds – their homes and roosts gone. Let’s not forget these same trees are carbon storage and carbon sinks releasing precious oxygen. Dead and ground into mulch all they can do is rot and release methane. Where are the climate champions, the greenies as these magnificent trees are lost. In the 20 years I’ve lived in Hazelbrook so many trees have gone just in my near neighbourhood. We are set for hotter summers with less cooling trees. The sound of chain-saws will be replaced by the hum of air conditioners powered by coal and gas as our town becomes just another suburbia bereft of its natural beauty, its trees.
Compulsory Vaccinations
Members of the wider community are discussing the need for workers and customers of various business to be double vaccinated, some discussions are more confronting than others with street protests and individuals behaving very badly.
Our Society is founded on the need for some individual restrictions for the safety of all. Workers at a construction site are required to wear fluoro vests, hard hats and steel-toed boots and wear long sleeve shirts. They are also required not to drink alcohol, take drugs or smoke in work areas. These restrictions are for the safety of all. Workers who work with children are required to have a “Working with Children Check” by Police for the safety of the children. Nurses and doctors working in hospitals and operating theatres are required to scrub up, wear fresh garments each day and wear appropriate personal protection equipment.
When we drive a vehicle on a public road we are required to wear a seat-belt, have passed a licence test, to not drink alcohol or drugs (ie under the influence of these) and obey the speed limit. Drivers also are restricted to designated parking spaces (you can’t park in the middle of a freeway) or drive through a shopping mall.
There are a myriad of examples where individual restrictions occur in society and we generally do not abuse these as they are always for the safety of the individual and those around us.
Science has shown over 200 years that vaccinations are effective against many, many diseases. The Covid pandemic has shown the safety of covid vaccinations in that almost 5 billion people have been vaccinated and relatively few have had major problems.
Those ending up in ICUs around the world are generally those who are now unvaccinated or those who have serious underlying medical conditions or are of an older age. If more people were vaccinated then even those with such co-morbidities, would be less likely to contract the disease.
Having a vaccination once or twice a year is far less onerous than having to gear-up every day to work on a construction site.
Yes, people in this society do have freedom of choice. If you choose not to get a driver’s licence then you can’t drive a vehicle; if you choose not to wear protective clothing on a construction site then you have made the choice to not work there. If you choose not to be vaccinated for whatever reason, then you choose not to work with me, not to attend the football with me, not eat with me in a restaurant and not travel on public transport with me.
Every choice we make in life has consequences. Make the choice and live with the consequences. As Jacquie Lambie, the Senator from Tasmania said, “Be a bloody adult!”
CANCEL CULTURE
Please read the article in The Good Weekend, the Saturday magazine of the Sydney Morning Herald of Saturday, 20th November 2021 on “Cancel Culture: It’s complicated” by James Button.
The article, to be presented over three issues of the Sydney Morning Herald viz Sat 20 November, Sun 21 November, Mon 22 November 2021, is the most definitive and best written exposé of this recent affliction to our society.
In my opinion, ‘Cancel Culture’ is not designed to change or remove ‘culture’ but instead to destroy any person, celebrity or not, who expresses an opinion that could cause hurt to someone, in many cases only the hurt of those who are the self-professed victims.
For hundreds of years, in our western culture the debate of ideas and opinions has led our institutions of learning and our governments and organisations. Debate where those involved listened to the ideas of others, put forward their own ideas and opinions and perhaps, but not always, came to an agreement or compromise. The debate was of the ideas not of the personal and people were prepared to allow all to profess their own opinions and thoughts as part of wider discourse.
But with the rising of social media, the anonymity of such avenues for expression of opinions has led to so much vitriol, such threats of violence, such cowardice that people so attacked have committed suicide or attempted suicide and at the very least have had their mental health severely compromised.
Please read the article with an open mind, be prepared to express your own opinions but DO NOT attack the author for his opinions.

Scam Text Messages
That “delivery” you just got a text message about is probably a scam.
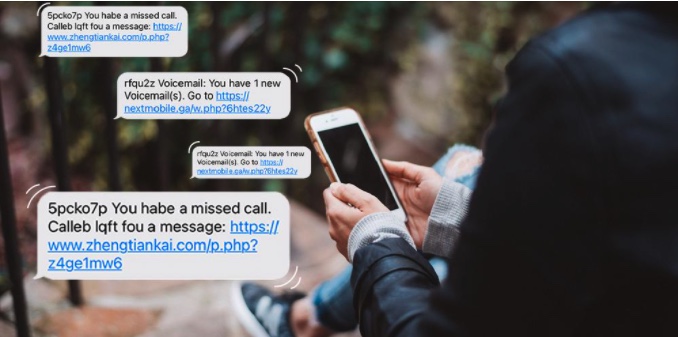
Over the past few months, many Australians have received a large amount of scam text messages and calls.
The bottom line – don’t click any of the links and don’t give your details away.
One of the many texts I have received over the past month were from ‘Australian Post’. This immediately rang alarm bells. Scam messages typically have spelling or grammatical errors (not all!) but these should at least have said ‘aus post’ or ‘Australia Post’. Scammers seem to rely on you not paying attention to the header and only reading the content. As to why anyone would click on a strange link, especially a php link is beyond me.
And as for the text messages from Craig Kelly, deluded Federal politician, are a disgrace. When I block the number, another comes from a seperate number.
Don’t get me started on the “robot calls” threatening police action if I don’t respond or the calls threatening to cut off my NBN. If I catch up to them, it won’t be their NBN I cut off!
Here’s a text message I recently got:

This is but one of the dozens I have received over the past month, all spoofing a different phone number and different link but all with much the same message. I deleted them all after first blocking the number. Probably not necessary to block the number as the scammers always spoof a new number.
Scamwatch are getting reports about text malware scams – if you receive a message like this DO NOT click the link! It is a #scam designed to download malware to your device. Delete the message immediately to #stopthescam Image and information via Scamwatch.
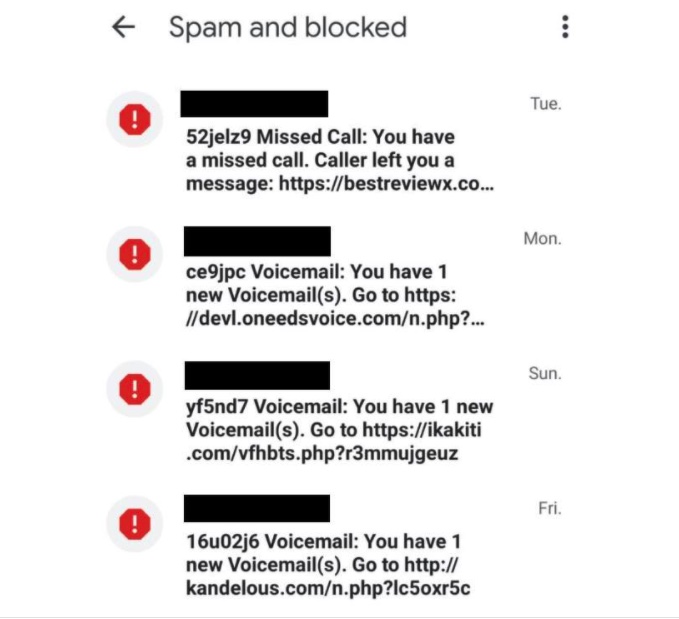
AUSSIES BEING INUNDATED WITH SPAM CALLS AND MESSAGES
Android malware called “FluBot” is infecting phones across Australia and clogging up our text and voicemail banks. FluBot is installed on Android devices by clicking a malicious link sent in a text message. Once it is installed, it has access to everything on your device, including bank details and passwords.
FluBot then uses your contact list to bombard your friends with similar scam links. These direct you to a web page posing as a trusted brand and encourages you to download an app.
The scam only affects Android users and only those who have enabled “side-loading”, where apps can be installed from outside of the Google Play Store. If you do not click text message links then you will not be affected.
To learn if your phone is infected, search for a new app called “Voicemail” with a blue cassette in a yellow envelope. If you attempt to uninstall this app, an error message will pop up – ignore it and delete the app.
Telstra may also contact members it identifies as sending exceptionally high volumes of text messages. Changing your passwords on a device you don’t believe has the malware will greatly enhance your security.
A factory reset can also be done if you do not believe your phone contained FluBot before your last backup.

Nine Perfect Strangers
- TV Mini Series
- 2021
- TV-MA
- Created by: John-Henry Butterworth
- Directed by: Jonathan Levine
- Based on the book by: Liane Moriarty
- Executive Producer/Showrunner: David E. Kelley

Starring:
Nicole Kidman, Bobby Cannavale, Regina Hall, Asher Keddie, Melissa McCarthy, Michael Shannon, Luke Evans, Tiffany Boone, Grace Van Patten, Samara Weaving, Manny Jacinto, and Melvin Gregg.

Nicole Kidman stars as Masha Dmitricher, owner and operator of a luxurious spa.
Could ten days at a health resort really change you forever? These nine perfect strangers are about to find out… Nine people gather at a remote health resort. Some are here to lose weight, some are here to get a reboot on life, some are here for reasons they can’t even admit to themselves. Amidst all of the luxury and pampering, the mindfulness and meditation, they know these ten days might involve some real work. But none of them could imagine just how challenging the next ten days are going to be. Can you stand to be in a room with nine people you don’t know?—augustdnl
Produced by Hulu, set in the USA but filmed in the hinterland of northern NSW in Australia and available as an 8-week series on Amazon Prime, the natural beauty of this Australian countryside is beautifully displayed.

There is a lot going on with these strangers as their past lives come alive over the series to show how each of them is in some way just a bit damaged, and in the same way, so is the staff headed by Masha. Her methods are unusual but the guests are quick to realise the tricks she uses and as her own past is revealed the drama intensifies.
I have enjoyed watching the first five episodes and look forward to the final three. The acting is very good and not overly ‘hammed up’ but Nicole’s fake Russian accent is a bit much. Intrigue, humour, drama…. It’s like a discovery voyage into the lives of the 9 strangers and the staff. Layers being peeled each time.

The Newsreader
The Newsreader provides an insight into the smoky Australian newsrooms of the 1980s and the people who brought us our nightly news.

This drama series premiered on Australian free-to-air channel, ABC on 15th August 2021. The series was created by Michael Lucas and stars Anna Torv, Sam Reid and Chai Hansen. It has six episodes and is set in 1986 in Melbourne.
The series blends together major news stories of the era with the lives and struggles, ambitions and careers and emotions and relationships of the cast.
Anna Torv play Helen Norville, the female co-anchor and newsreader of the Six O’Clock News. She is an emotional wreck, relying on prescription pain-killers and sleeping pills but once the camera starts she is the perfect newsreader. Her senior co-anchor/host is the ageing, heart-attack candidate (smoking and drinking) Geoff Walters, played by Robert Taylor, a seasoned journo who made his name in the field of wars (Vietnam) and conflict (The Dingo Took My Baby). The inference is that “glamour” and Helen’s brand of more “emotional” news coverage is replacing a more staid kind of impartial journalism.
The young, ambitious field reporter, Dale Jennings, played by Sam Reid, finds himself in a relationship with Helen Norville when she has a breakdown and takes an overdose. Jennings has his eyes set on being a news host bumbling his way through until a lucky chance places him near the terrorist bomb blast in Melbourne in 1986 and he is able to show his raw talent.
But not all is going his way when he has an encounter with his gay cameraman, Tim Ahern (Chai Hansen) and doubts his own sexuality. He says he choses Helen because he cares for her but in reality he is most likely denying his true self in an era when being gay was not only illegal but also career ending.

Stephen Peacocke plays a stereotypical sports reporter, Rob Rickards and also stereotypical is the blustering news boss Lindsay Cunningham played to excess by WillIam McInnes. The newsroom is more racially diverse than any newsroom of the time with Michelle Lim Davidso playing Noelene and Chum Ehelepola as Dennis.
Great cast, script, direction, cinematography, editing etc. Plus the bonus of major world news events from 1986. The newsroom is a ruthless arena and only the strongest gladiators will survive.
It’s showing the changing of the guard from the old style of news reading to today’s double header desks with sports and updates, of heavily repeated footage and the drama.

Available to watch Sunday nights live and streaming on iView. Well worth it!
What Is Smishing and How to Avoid it
Perhaps you’ve heard of phishing. This is the criminal practice of using fake emails to defraud users into giving away sensitive personal information such as passwords or bank details. Well there’s more than one way to phish – one of these being “smishing”. This entails using fake SMS (mobile phone text) messages to gain your personal info. But don’t swim into despair just yet, there are still ways to protect yourself.Download AVG AntiVirus FREE

The psychology of smishing
The more things go mobile, the more prevalent smishing will be, so it’s important to hone your hackles to rise upon receipt of a devious text message. While people have gotten used to email spam, they are probably less likely to doubt the legitimacy of an SMS message.This article contains:This article contains:
- The psychology of smishing
- How do smishy numbers look?
- How a smish might occur
- Avoid smishing with these tips
Smishers rely on your quick reaction to a message that may appear basically identical to an actual message from, for example, your bank. One tactic – or tip off – of a fake message is the imploring of an immediate response such as,“Urgent!” or “Reply now!” The less you think, of course, the better for the scammers. However, even if you give the message a good look-over, it could still fool you.
How do smishy numbers look?
While some smishes come from strange phone numbers, fake messages can simply use the name of a business instead of a visible number – the way many real businesses already do. One such tricky smishing scam happened in the Czech Republic with a text that really appeared to be from their postal service. Further complicating the matter is the fact that many real businesses will use a “shortcode” to send text messages. This is a small group of numbers that appears instead of a real phone number – and yes, scammers use similar brief numbers to their heart’s content. And yet even more dastardly is that sometimes the fraudulent messages can insert themselves into your existing legitimate message threads! Yes, things can get a bit bleak, but press on, heroic reader, and you’ll find ways to arm yourself with knowledge and train yourself to recognize certain tells of fake messages.
How a smish might occur
Here is how an especially slippery smishing scam might go. You get a message from what appears to be your bank telling you to download their new app. You click a link inside the message, and a web page opens up that looks exactly like your bank’s website – or at least how you imagine your bank’s website would look (who can remember anyway, since things look different on mobile, and banks aren’t known for having scintillatingly memorable webpages anyway).
So now you’re on this official-looking page that doesn’t have any raging signs of anything phishy. You are simply shown a button to download a banking app. Well, slick as this whole operation is, you might be able to spot one problem, which is that the link doesn’t show the label for the Google Play or Apple App Store. Now Apple won’t innately let you download apps that aren’t on their App Store, but Android phones are more susceptible to malware downloads. But in both cases, these stores have a careful verification process, so there’s less chance a piece of pure malware would be there (though it has happened).
If you’ve already clicked your way to this initial download screen, the smishers still don’t have you completely hooked – you can still slip away by not downloading the fake app. But if you do download the fake app, you can really get into some hot water. Once downloaded, that app will likely prompt you to enter your bank info – and those details are then delivered right into the hands of the hackers. Or, in the particularly nasty case of the aforementioned Czech Post smish, the newly downloaded fake app – full of juicy malware – disappeared and created an overlay to appear in the user’s other apps, prompting, yes, credit card info to be entered, and the rest is history.
Avoid smishing with these tips
- If the message is clearly from a number you don’t know, or a company you know you don’t have business with, don’t click on any links within. Simple, but effective.
- Whether you’re worried about smishing or not, an eternal rule of thumb for existing more securely on the internet is to have different passwords for different accounts. Yes, this can be annoying when you’re trying to quickly hammer in the right password, but password managers can help with that, and it pays off in the long run in the event that you do get compromised by a scam.
- Get AVG AntiVirus FREE, which can recognize phishing websites and prevent you from clicking your way to doom.Download AVG AntiVirus FREEGet it for iOS, Android, PC
- Be cautious of strange-looking numbers, but remember, as mentioned above, strange-looking numbers can still be legitimate, so really think before you click onward – and never click if you’re in doubt. Doing a quick search online for the number in question may reveal it to be a scam number.
- Messages containing: “Congratulations, you’re a winner!”; “Urgent!”; and “Reply now!” are not things you should ever pursue further.
There is a lot of strange phishing in today’s digital ocean. While you may get fooled, arming yourself with knowledge is a great defense. by Colin Asher on January 23, 2020
by Colin Asher on January 23, 2020
Updated on August 26, 2021
Signs Your Phone Has Been Hacked
With your contacts, credit cards, banking info, and more stored on your phone, you may ask yourself: Can my phone get hacked? Sadly, cell phone hacking is indeed a problem, and a hacked phone can cause serious issues. Learn how to detect phone hacking and protect yourself with a free mobile security app.Install free AVG Mobile Security
/Signal-Signs-your-phones-been-hacked-Hero.jpg)
Can someone hack my phone?
Yes, your phone can be hacked — and it happens more often than you might think. But there are ways to tell if you’ve been the victim of a phone hack, and precautions to take to avoid being hacked in the first place.
In this article, we’ll show you how to protect yourself against phone hacking.This article contains:This article contains:
- Can someone hack my phone?
- How to know if your phone has been hacked
- The techniques phone hackers use
- My phone was hacked, how do I fix it?
- Protect your phone against hacking
How to know if your phone has been hacked
There will always be hackers, but you can keep your data safe by watching out for signs of foul play. Here’s how to tell if your phone has been hacked.
/icon_01.svg) It’s running slower than usual
It’s running slower than usual
One of the most common phone hacked signs is a drop in performance. If websites are taking too long to load, or if your apps are suddenly crashing when you use them, malware may be hogging your phone’s bandwidth or processing power. You may also experience trouble with sending and receiving messages or when trying to turn your phone on and off.
/icon_02.svg) Your phone feels hot
Your phone feels hot
Does your phone ever feel hot, even when you haven’t been actively using it? Phones can heat up during prolonged periods of intensive use, like while streaming a movie or gaming for hours, but if it’s not you that’s causing your phone to heat up, it may be someone else.
/icon_03.svg) You’re draining battery faster than usual
You’re draining battery faster than usual
If your phone’s battery is draining faster than usual, check if you have a lot of apps open in the background. Background apps can burn through lots of data, and you can save battery power by restricting background app data.
There are many ways to make your battery last longer, but if everything is otherwise normal, shorter battery life may be a sign your phone has been hacked.
/icon_04.svg) Service disruptions
Service disruptions
While it isn’t uncommon to occasionally experience a dropped call or a bad connection, if service disruptions have become increasingly regular, it may be time to ask: Is my phone hacked?
/icon_05.svg) Strange pop-ups
Strange pop-ups
If you’re seeing a lot more pop-up ads than usual, your phone may be infected with adware, a type of malicious software that inundates you with ads. Never tap any suspicious ads or links.
/icon_06.svg) Websites look different
Websites look different
Sometimes Google will change the look of their homepage for a special day, but if you’re noticing that many sites look different than they usually do, it could signify a hacked iPhone or Android.
Malware on your phone could be acting as a proxy between you and the web, redirecting your traffic to other sites. Knowing how to check if a website is safe can help you protect yourself.
/icon_07.svg) New apps appear
New apps appear
While we’ve all downloaded an app and then immediately forgotten about it, one of the signs a phone hacker has accessed your phone may be the presence of apps you don’t recognize. In a messy phone library, a single extra app with malicious intent may go unnoticed.
If you see an unfamiliar app, look it up online — you may need to remove malware from your phone. And make sure to assess apps for safety before downloading them.
/icon_08.svg) Apps stop working properly
Apps stop working properly
If your apps are frequently quitting, or your phone is regularly freezing up, it may be because your cell phone was hacked and malware is using up your phone’s resources.
Poor performance could also signal that you need to update your phone’s software, which is essential for phone security. Before shelling out for a new phone, try our tips to speed up your iPhone or boost your Android.
/icon_09.svg) You receive unknown calls and texts
You receive unknown calls and texts
Can someone hack your iPhone through text? Can someone hack into your phone by calling you? It’s unlikely someone can directly hack your phone by calling you (though they could attempt to phish for information), but text hacking is another story.
While many hacked text messages require you to click on a suspicious link, an iPhone message hack with interaction-less iOS bugs can use a text message to infect your phone, even without you doing anything. You can protect against these exploitable vulnerabilities by using an encrypted messaging app to keep the data secure.
If someone tells you that you’ve called or texted them when you haven’t, it’s likely your phone has been hacked. Inform friends and family if you receive strange messages or calls coming from them.
/icon_10.svg) Running out of data
Running out of data
If you’re noticing unexplained spikes in your data usage, you may not be the only one using your data. A hacked iPhone or Android device can use your data to transmit information collected from your phone.
/icon_11.svg) Unexpected bill charges
Unexpected bill charges
If you have unexpected charges that your phone company can’t account for, they may be coming from the extra data usage described above. If someone is using your phone remotely, they could be calling people or using premium services. Mysterious charges should be investigated to rule out malware.
Fleeceware apps can charge outrageous subscription fees and may also be the cause of your billing issues. These apps usually lure you in with a free trial, which turns into a paid subscription a few days later. If you find one of these on your phone, unsubscribe from within the app — simply deleting it won’t work.
Protect your phone against threats like these with AVG AntiVirus for Android or AVG Mobile Security for iPhone. Both apps offer an additional layer of protection against hackers and will secure your phone and protect your personal information.Install free AVG Mobile Security
The techniques phone hackers use
So how are these hackers able to get into your phone in the first place? The most dangerous and famous hackers use a mix of technical wizardry and social engineering tricks to exploit the humans behind the phones.
/Hacked-phone.png?width=1319&name=Hacked-phone.png) Phone hackers can use a variety of techniques to infiltrate your mobile device.
Phone hackers can use a variety of techniques to infiltrate your mobile device.
Here are some of the most common techniques hackers use to hack phones:
Phishing
Phishing involves using social engineering tactics to fool you into disclosing personal information. A phishing attack can be simple, like an email with a link that says FREE and directs you to a malicious site. Many of today’s most famous hackers use phishing attacks in their campaigns.
Or it can be a more complex scheme, like an online quiz that can tell you which Disney princess you are based on your birthday, mother’s maiden name, and the name of your first pet — answers which the attacker can then use to break into your accounts.
Phishing can also be highly targeted, focused on tricking one specific high-level employee into revealing too much information. Focused attacks against senior leadership figures are known as whaling.
Spy apps
One sneaky way to infect a phone with malware is to convince someone to download an app with hidden spy features. This app may be disguised as a game, an app for productivity, or even one promising security, when it’s actually a spyware app tracking your online activities and personal data. Some Android spyware can even spy when your phone isn’t on.
Another type of malicious software for your phone is stalkerware, which tracks your movements, browsing, messages, and calls. Stalkerware is usually installed by someone close to you — when parental control apps are used in this way, they become stalkerware.
Make sure to remove spyware from your Android and get rid of creepy spying apps on your iPhone.
SIM swapping
Many two-factor authentication (2FA) procedures confirm your login with a text message sent to your phone. With SIM swapping, hackers try to convince your service provider that your phone number actually needs to be swapped over to a different SIM card (the hacker’s). That way, they’ll receive your authentication messages.
SIM swapping scams usually starts with phishing attempts designed to give the hacker enough information to impersonate you to the service provider. With enough of your personal info, a hacker can use your phone number to initiate a SIM swap.
While it’s unlikely someone can hack into your phone by calling you, you should still protect your phone number: an unknown call now may be part of a plan to hack later.
Unauthorised access
Cybercriminals can use phishing or other techniques to access your iCloud or Google account. Many people have these accounts linked to their social media, which can be leveraged as a vulnerability to get into your data. With unauthorised access to your accounts, a hacker can see your location information and view your emails, messages, and keychains.
Bluetooth
It may make it easier to play music through a speaker, but a wireless Bluetooth connection makes your phone more vulnerable to cyber crime. Hackers can use software to intercept a bluetooth signal and gain access to your phone. Don’t pair your phone with a device you don’t trust, or in a location that’s unsecured.
Wi-Fi
Similar to Bluetooth, Wi-Fi can also be used by hackers to gain access to your phone. In particular, using public Wi-Fi networks can leave your phone vulnerable to attack, as they may have been set up by a malicious actor waiting for you to connect. It’s also important to change the default password to your home Wi-Fi network to prevent hackers from hacking into your router.
You can protect yourself on public Wi-Fi by setting up a mobile VPN on iPhone or Android. A VPN, or virtual private network, encrypts your connection to prevent bad actors from getting into your phone.
Charging stations
Need to quickly charge your phone at a public charging station? Think twice — the juice jacking scam infects these stations with malware to target people running low on power.
An infected charging station does more than give you a power boost. The malware spreads to your phone, where it can monitor what you do, collect and transmit your private data, and even make a withdrawal from your bank account.
If you use mobile charging stations, protect your phone with a cybersecurity app from a trusted provider. AVG AntiVirus for Android and AVG Mobile Security for iPhone keep your phone safe from malicious activity, ensuring that your data and apps are always protected.Install free AVG Mobile Security
My phone was hacked, how do I fix it?
If you think your phone has been hacked, there are ways to find and remove malware on Android phones or iPhones — you can remove malicious apps, clear your cache and downloads, or even fully wipe your phone.
But the safest method is to protect your phone against hacks in the first place with one of the best free antivirus apps available.
Protect your phone against hacking
Even if you’re always careful, hackers are constantly building new hacking tools to get into your devices. If you’re an iPhone user, AVG Mobile Security for iPhone/iPad will keep you safe by automatically checking that your Wi-Fi network is secure, as well as monitoring online databases to ensure none of your passwords have been stolen.
AVG also offers powerful protection for Android devices. AVG AntiVirus for Android protects your phone from malware, unsolicited calls, and other malicious behaviors. It also gives you additional anti-hacking protection by locking apps with sensitive information. Plus, anti-theft defenses help you locate and even wipe your phone remotely if it’s ever lost or stolen.Install free AVG Mobile Security
by Samuel Kellett on May 13, 2021
Updated on July 16, 2021






