Genealogy and DNA
DNA and genealogy are two topics that are closely linked. Together, they provide an invaluable resource for those interested in researching their family history.
DNA, or deoxyribonucleic acid, is the genetic material found in all living things. DNA contains the instructions for the development and functioning of all organisms. It is made up of four chemical components known as nucleotides. Each nucleotide contains a specific sequence of genetic code, which is unique to each individual.
Genealogy is the study of family history. It involves researching one’s ancestry to uncover information about their ancestors. Genealogists often use records such as birth, death, marriage, and military records to trace their lineage.
DNA and genealogy have become increasingly intertwined in recent years. DNA testing has made it possible to identify and trace family lines with unprecedented accuracy. Through the use of DNA testing, genealogists can find new information about the origins of their family and its members. This information can be used to confirm or refute traditional genealogical records.
DNA testing can also be used to identify distant relatives and match them to existing family trees. This can be done through a process known as genetic genealogy. Genetic genealogy involves comparing DNA sequences of the tested individual with those in the database e.g. Ancestry.
STOP, THINK & RUN – Stop Innocently Giving Your Information to Cybercrooks on Social Media
Beware; Take Care

STOP, THINK & RUN – Stop Innocently Giving Your Information to Cybercrooks on Social Media
Posted on May 20, 2022
Yes – you. All of us. This article is written for and applies to everyone.

We are all targets for social engineering which is the act of manipulating, influencing or deceiving people into performing actions or divulging confidential information – generally by engaging you or manipulating your emotions.
The most skilled cybercriminals accomplish their goal without you even being aware of what’s going on. You’re relaxed and just enjoying yourself, checking your social media news feed. No Nigerian princes needed anymore. They’ve moved on, taken on new personas, but are still targeting you.
Literally, everyone is a target.
The Bad Guys Kicked It Up a Notch
The bad guys have improved their skills. Attackers find loopholes and opportunities where you least expect them. They gain your trust or take advantage of your defenses being down – and they are very skilled at what they do.
I see people who I would think should know better engaging in risky behavior every single day, probably because they aren’t aware that the nature of the threats has evolved and changed. The bad guys stay one step ahead of us.
Please read this article even if you know what you’re doing. Someone you care about may not and you can help them.
Social Media
We all want to use social media and public platforms for genealogy and communicating with family and friends. We need to realize that because of the open nature of those platforms, they are full of bad actors trying to take advantage of us in seemingly innocent ways.
Not to mention that the platform is free for users, so access to you IS the commodity. Not just through ads, which you can clearly recognize as such, but by manipulating your behavior.
How, by luring you with “free,” “fun” or “missing out.”
Seriously, you do NOT need a new “free” improved profile picture.
Furthermore, some unnamed person or site you don’t know doesn’t really care about the TV show you watched when you got home from school as a kid.
Well, actually they DO care, but it’s not innocent. Scammers and bad actors gather, aggregate, and distill data about us hoping to breach our electronic security – and/or that of our social media friends.
Even if the person or account asking isn’t malicious, if the post is public, cybercriminals can and do gather and compile information about YOU that they find on public postings and pages.
Why?
In an attempt to defraud you, AND your friends who will also fall for these schemes. If your friends see you do something, they are more likely to engage in the behavior themselves. Just the act of answering these seemingly innocent questions conveys information about you.
- First, you’re vulnerable and don’t understand that “public posts” and resulting answers make you a target. In other words, you’re advertising that you’re a good target.
- Second, if you don’t have your Facebook (or other social media) account locked down so that only friends of friends can send you friend requests, it’s not unusual to receive a whole raft of friend requests after doing something public.
- Third, even if your account is locked down tight, your comment or answer to that seemingly innocent public posting may net you a reply something like this:

Note the bad grammar and lack of punctuation. Probably that Nigerian prince again, with a bogus profile picture.
If people can see your “About” information, the message or reply may be more specifically tailored – targeting you with some common interest. Single middle-aged female? You’ll receive a message from a “widowed” male about that same age, maybe wearing a uniform or otherwise looking like a model, holding a puppy. Yea, right.
Now, holding the 1890 census – that might be an effective scheme to target genealogists
Let’s talk about how to stay safe and still be able to benefit from and enjoy social media.
We will begin with a big red flag.
NewProfilePic
The current rage is an artificial intelligence oil painting profile picture that’s “free.”
Right off the bat, you need to always be suspicious of anything “free” because it often means “they,” whoever they are, want your information and are willing to give you something to get it – under the guise of free. Speaking of them, just who are “they” anyway? That’s the first question you need to ask and answer before engaging.
Free almost always never benefits you.
Why would anyone want to give you a cool new profile picture for free? It may only take a few computer cycles, but it’s not free for them to produce, just the same, especially not when multiplied by the tens of thousands. What are they getting out of all those free photos they are producing?
I’ll tell you what. To gain access to your data – including the data on your phone.
Hmmm, I want you to think about something for a minute.
Do you have your phone set or apps set to scan your face and automatically open? Is that your security? For your bank account maybe too?
And you just sent a photo of your FACE to some unknown person or group in some unknown place?
Really?
You can change a lot of things, but you cannot change your face and facial recognition software is powerful.
Snopes says the NewProfilePic app really isn’t any worse than many other apps – which isn’t saying much.
Aside from the fact that NewProfilePic was initially registered in Moscow, which should be a HUGE red flag by itself, especially right now, what can the app do on your phone?
Here’s the list.
In essence, you just gave someone the keys to the candy store.
In perpetuity.
Is your blood running cold? It should be.
Still think this fun new app is “free?” You’re paying for it dearly, and may yet pay for it even more dearly.
Here’s a warning from a state Attorney General and here’s an article from MLive that interviewed a cybersecurity expert who notes that this app scrapes your Facebook data.
However, so do other people and apps.
Public is Public
When you see anything on Facebook with the little globe, that means that anyone anyplace can see this posting AND all replies, including your answers. Everything is fully public.
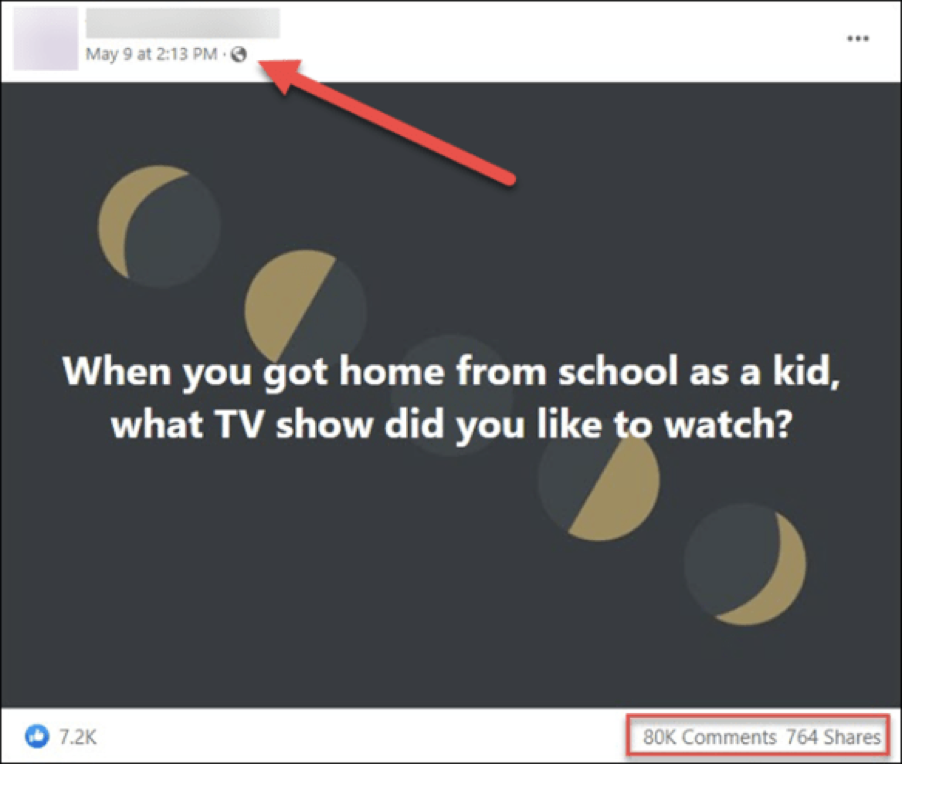
In this case, more than 80,000 people answered this question from an entirely unknown person or website.
Just a couple of days later, this same posting had 54K likes, more than half a million comments, and more than 6,100 shares. That’s how effective this type of seemingly innocent question can be.
Several of my friends answered.
What does this question tell anyone looking? Your approximate age, for beginners.
Maybe an answer to a security question. Just google “top security questions for gaining access to forgotten passwords.”
Engaging with a web page also means the Facebook algorithm will send you more postings from that website in your feed. So maybe if this post doesn’t yield anything useful about you, the next one might.
Cumulatively, many answers to many postings will reveal a lot.
Never answer these.
But There’s More
Because this posting is public, I can click on the name of ANY person who has answered that public question and see every other public thing they’ve shared on their timeline.
As an example, I randomly selected Charlotte, someone that I don’t know and am not friends with who replied to that question. (You can do this same experiment.)
I clicked on her name and scanned down Charlotte’s postings. I can immediately see that she’s a good target and has fallen for several other things like this.
Here’s one from her page.

That scammer, James, latched onto her immediately. Again. Note the grammar.

Here’s another seemingly innocent game that Charlotte played to get a new Facebook profile picture and “secret” info about herself. That “4 Truths” app told Charlotte that she was very mysterious and promised to “show what’s hidden in you.” Of course, she had to provide her photo, give permission for this app to post on her timeline, publicly, and access her Facebook account. Charlotte probably didn’t even realize that was happening, or what it meant was happening behind the scenes to her data.
But now Charlotte has the new NewProfilePic oil portrait, so this one isn’t in use anymore. Maybe Charlotte’s friends wanted some nice things said about them too so they might have clicked on this same link. Just for fun, right? That’s how these scams work.
These unfortunate choices on Charlotte’s timeline were accompanied by many more that were similar in nature. Those were interspersed with notices on her Facebook page that she has been hacked and not to accept any new friend requests or messages from her. The effects are evident.
It’s worth noting that some people do have their profiles cloned and haven’t engaged in any risky behavior like this, However, you dramatically increase your odds of being compromised when you engage in risky online behaviors. Every time someone clones your profile and sends messages to all of your friends with malware links, it increases the cyberthief’s harvest of you and your friends. Cha-ching!
Eventually, the bad actors will find people who they can scam, either by:
- Talking your friend, their target, into doing something bad for them, maybe thinking they are helping you or responding to you
- By sending malware links that people click on thinking the message with the link is actually from you.
- Gathering enough information to breach you or your friends’ security questions and clean out bank accounts.
No, I’m not fearmongering or being overly dramatic.
I utilize KnowBe4, a security and vulnerability consulting and training company to keep abreast of threats. You can follow their blog articles, here.
How Do Cybercrooks Access Your Friends?
Looking at Charlotte’s Facebook page, all of her friends are exposed too because they are publicly visible. Everyone can view the entire list of Charlotte’s friends.
Now, all of those scammers have access to Charlotte’s friends. Hence, the scammers can clone Charlotte’s account by stealing her photo, setting up a new account, and sending messages to Charlotte’s friends who think the message is from Charlotte. Something like “Try this new photo app, I did,” or, “Can you pick up an Apple gift card and send it to my friend for me?” You get the drift.
If Charlotte’s friends have their security set to only accept friend requests from someone that also shares a friend, and Charlotte accepts a bogus friend request – then the scammer can send her friends a friend request too and they think it’s Charlotte’s friend.
In other words, seeing a common friend causes Charlotte’s friends to let their guard down. I look at it this way – only one of my friends has to accept a bogus friend request to make me vulnerable too.
Charlotte also told people in a public posting that she was visiting someone on a specific day in another city. How do I know it’s another city? Because Charlotte has posted where she is from, where she lives, works, and the high school she attended in her “About” information.
Hmmm, those are security questions too.
That same website where I found Charlotte answering that question has also posted questions about your pet names.
What is one of the security questions if you lose your password?
Yep, pet names.
Nope, those seemingly cute sites aren’t. They are data-mining and gathering information.
Predatory Sites
First, I need to say that there are three security threats involved with these postings and websites:
- Any link you click which may take you to who-knows-where.
- That the site itself is data mining. However, this is not always the case. Some very legitimate companies ask questions to get you to engage in their subject topic. However, if the post is public, that’s an open door to the next threat.
- “People” or bots who harvest information about people who answer those public posts and then data-mine their accounts.
Let’s look at a few examples.
No person you don’t know cares at all about what you drank last. However, that might be valuable data for other reasons.
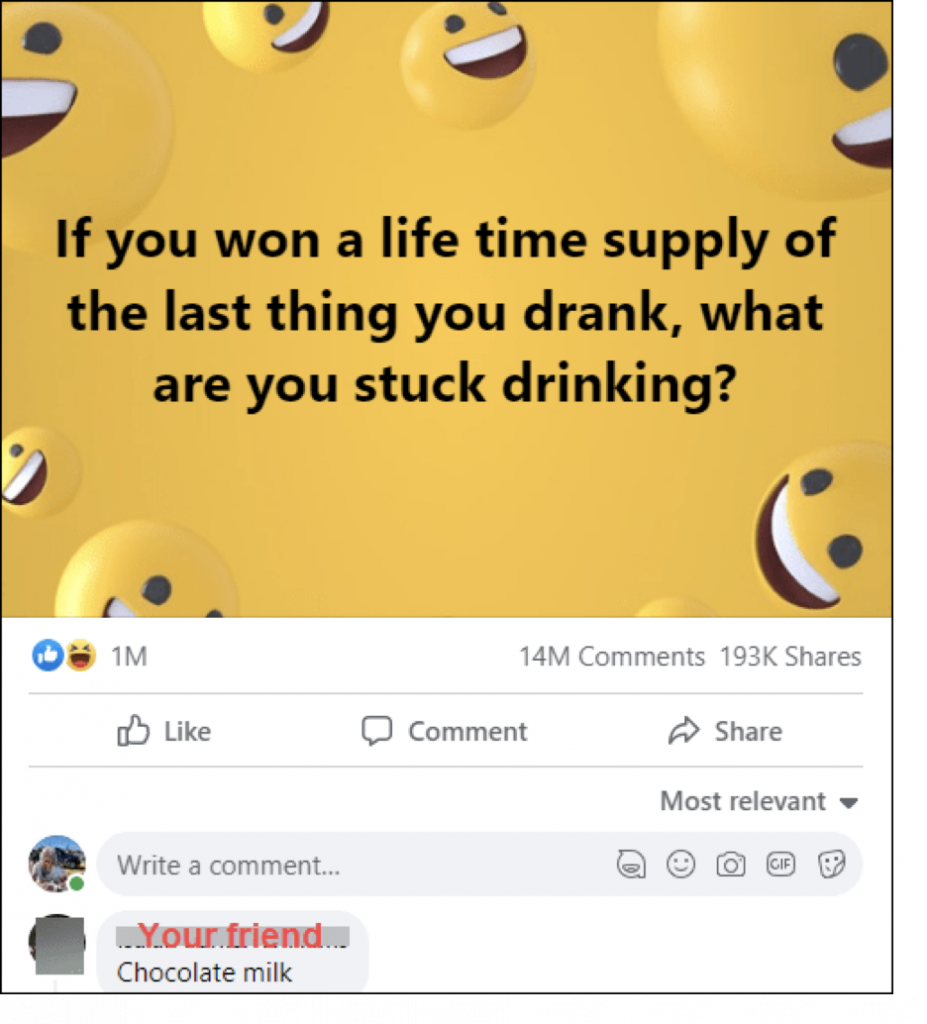
Facebook makes these things even more attractive to you by showing you answers from people on your friends list. I’m not going to embarrass my friends and family by showing their identity, even though it is completely public, but please, FOR THE LOVE OF ALL THAT’S HOLY, stop doing this.
Just look at that – 14 million comments and 193 thousand shares. For a data miner, this has been extremely successful.
To make matters worse, if you engage with a site on Facebook, they show you more from that site in your feed in the future. Since I clicked on these to write this article, my feed is going to be flooded with smarmy questions from these sites for days or weeks.
Let’s take a look at a few more examples.

Look at this one. 200,000 people and almost 3000 shares in two months. That means that this question appears on 3000 people’s timelines. It’s like a huge data-gathering pyramid scheme.
You’re likely to be wearing your favorite color and eat your favorite food.
How could this be used against you?
Yep, security, password, or account recovery questions again.
When I went to the page that made this posting, the next posting was a question – “In 1980, you were…” and the first person to answer said, “2 years old.” That person just told the world they were born in 1978.
Did you really want to do that?
Private Groups
You are safer in a private group, meaning only group members can see your posts.

You can tell if a Facebook group is private based on the lock and the words, “Private Group.” You can also see a list of your friends who are members of that group as well. Remember that the criterion for joining a private group differs widely and there are still lots of people you don’t know. Some private groups that I’m a member of have more than a quarter-million subscribers.
Most private groups are focused on a specific topic. Some private groups require answering application questions to join, and others don’t.
You’re safest in a group that does require questions to be answered which allows administrators who are familiar with the topic to craft questions that (hopefully) weed out most of the trolls, bots, and shady characters. That’s the choice I’ve made for the groups I co-administer, but it does require more attention from the administrators, which is why large groups often don’t implement membership questions.
Determining Privacy Settings

When you’re looking at the privacy settings on groups, posts on your friends’ timelines, or your own, you can mouse over the privacy icon. Facebook will tell you exactly who can see this post.
You’re never entirely safe. In addition to behaving safely as noted above, there are steps you can take to educate yourself and configure your social media accounts securely.
How to Stay Safe
Every social media platform is different, but I’m using Facebook as an example. Every platform will have a similar privacy function. Learn how it works.
Go to the Facebook help center, here and do a security checkup, here.
However, neither of those really address privacy, which I feel is actually the biggest security threat – the trapdoor or slippery slope.
Here’s how to access and review your privacy settings.

Click on the down arrow beside your name.

Click on Settings and Privacy, then both the Privacy Checkup and the Privacy Center.
Next, you’ll see several short articles. Be sure to step through each one
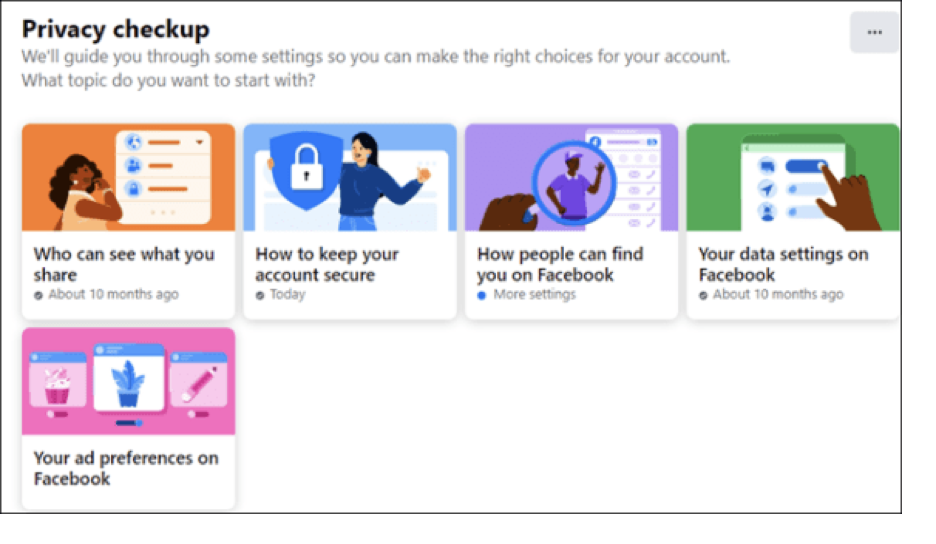
Take a few minutes to lock your account down.
The ONLY thing that is automatically public is your profile photo and any photo you use for your cover photo. Anything else can and should be restricted.

Facebook owns Instagram so you can set your Instagram security here too.
You’re not quite finished yet!
Monitoring and Controlling Apps
Next, we’re going to see what apps are installed and interacting with Facebook. Have you authorized apps you weren’t aware of?

In the dropdown arrow to the right of your name in the upper right-hand corner, click on the down arrow again.
You’ll see the Settings gear under “Settings and Privacy.” Click there to see all of the setting categories in the panel on the left side of your screen.
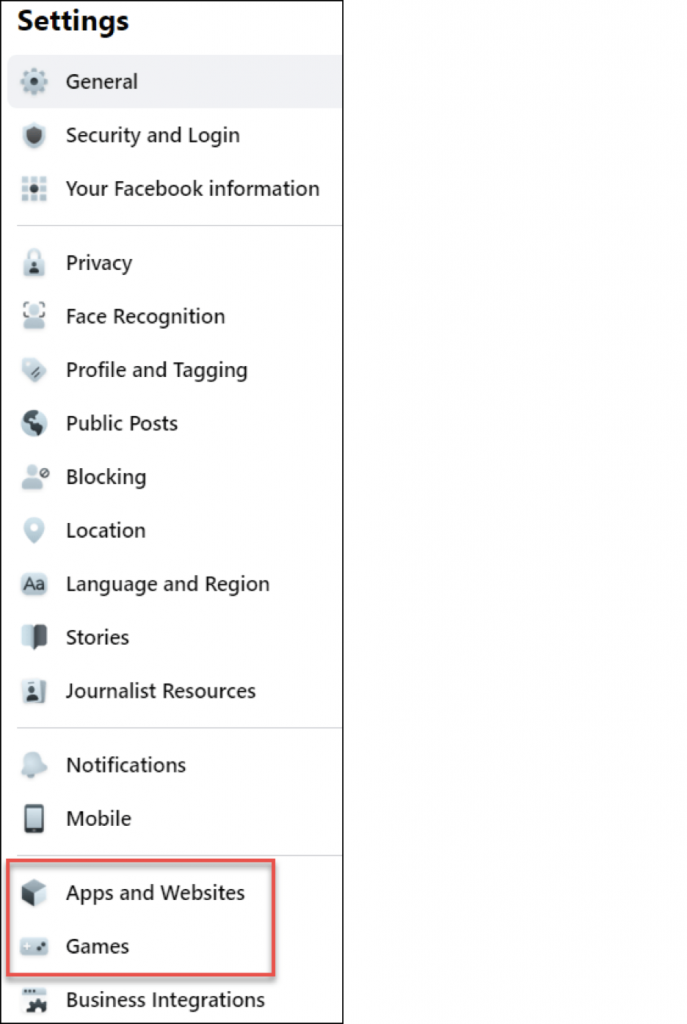
Review everything, of course, but pay special attention to “Apps and Websites” and “Games.”
Predatory operators will fool you into doing something fun, like a profile photo app, or a little game that provides you with your Fantasy Name or something else cute and enticing. That “free” game or app installs software. If you find software during your review, especially from something like we’ve been discussing, I recommend deleting it immediately.
Be sure you only have things you’ve intentionally installed or authorized.
THINK – Stop, Think and Run
When you see “someone” asking a question on Facebook, STOP!
You’ve heard of stop, drop and roll if your clothes are on fire?
Someone trying to breach your privacy is a digital fire, so this is stop, think and run.
Think about who is actually asking and why. “Who” is asking is NOT that cousin who shared the question from that public site. The “who” that is asking is that original site. They are simply taking advantage of and using your cousin. I hate to put it this way, but always assume the worst and remember that even if the site itself is innocent, all of the people who can harvest your data and try to compromise your security assuredly are not.
Those “fun” sites asking those questions are either actively recruiting you or best case, leaving the door wide open for cyberthieves.
Don’t answer. No matter how much you’re tempted to share some nostalgic information or the name of your deceased pet you’re still grieving. No matter if you notice that your cousin or friend has replied already. Just don’t.
Stop, think, run. It’s that simple.
And speaking of your cousins or friends – if they have shared something that could compromise their security and privacy, not to mention their friends (including you), feel free to share this article or others, such as KrebsonSecurity. Take a look at Krebs’ examples of baiting you with childhood and puppy photos with corresponding questions. Do they evoke an emotional response from you? They are meant to. I mean, how bad can it actually be to enter the name of your beloved childhood pet?
By now, you should be screaming the answer to “how bad”!
Here’s an article from Tulane University. Yes, they are advertising their degree in cybersecurity management, but they do so by summarizing the things that social media users need to be concerned about.
I also follow a company called Facecrooks which monitors and writes about Facebook privacy, fraudsters, other scams, and such. They have a Facebook page here and a Scam Watch page here.
The Baker’s Dozen Messages
The messages I want to leave you with, aside from stop, think and run, are this:
- Nothing is free
- Think before you engage or answer
- Remind yourself that a stranger really doesn’t care about your first-grade teacher’s name, but a crook does
- Just because someone you know answered or engaged doesn’t mean it’s safe
- Consider potential consequences
- Can something you are about to share be used to compromise either you, your family, friends’, or employer’s privacy or safety?
- Don’t overshare – only say what’s necessary
- Notice what is public and what is not – look for that globe and behave accordingly
- Don’t download or play free games, or send anything to a “free” website
- Don’t click on links to unknown places
- Don’t accept friend requests from people you really don’t know.
- Learn the warning signs of a fake profile and report them by clicking on the three dots to the right of the profile
- Don’t click on links in private messages and beware of suddenly receiving an “odd” message from someone you haven’t heard from in a while
I’ve written other articles about online privacy, security, and safety too.
- Stay Safe: Phishing Moved to the Next Level – Meeting Invitations and File Transfer Links
- Genealogy, Identity Theft and Equifax Update
Remember…
Stop. Think. Run.
Explore over one million historical newspaper pages for FREE
In partnership with the British Library, FindmyPast have made over a million newspaper pages completely free to search and view. And there’s much more to come…
Following their renewal of a long-term partnership with the British Library, together they have pledged to make millions of historical newspaper pages free to view online. Search FREE newspaper archives
Over one million pages are now free to search and explore on both Findmypast and their sister site, the British Newspaper Archive. This will be expanded by more than 2.7 million additional free pages over the next four years.
Originally launched in 2011, Findmypast and the British Library’s partnership has delivered the most significant mass digitisation of newspapers the UK has ever seen. The British Newspaper Archive and Findmypast are currently home to more than 44 million fully-searchable pages from over a thousand regional, national and specialty titles dating from 2009 all the way back to 1699. Their ever-growing digital catalogue covers every corner of the British Isles as well as a number of former British territories including Canada, New Zealand, India, Pakistan, Barbados and Jamaica.
Previously, this vast cultural treasure was held entirely in hard copy and microfilm, meaning travel and hours of painstaking manual research for anyone wishing to explore its contents. Now anyone, anywhere in the world, can uncover millions of articles across hundreds of titles, in just a few simple clicks.
What newspaper archives are free?
There are currently 158 free newspapers on offer, dating from 1720 to 1880 and covering a diverse array of histories, locations and topics. The newspapers selected were digitised as part of four special British Library projects:
- 19th Century Newspapers: a project funded by the Joint Information Systems Committee and the British Library’s first major newspaper digitisation programme
- Heritage Made Digital: an ongoing project to transform digital access to rare and early newspapers, focusing on newspapers in a poor or unfit condition
- Living with Machines: another ongoing project, jointly led by the Library and the Alan Turing Institute, which has been digitising selected UK regional newspapers as part of a major study of the British industrial age and using artificial intelligence tools to undertake new kinds of historical enquiry
- The Endangered Archives Programme: a project that facilitates the digitisation of archives around the world that are in danger of destruction, neglect or physical deterioration
Illuminating diverse stories
Many of the papers included have been specifically chosen to help you shed new light on diverse and previously underrepresented communities and their histories. Highlights from the collection include:
- Barbadian (1822-1861) – a fascinating Caribbean publication that covers the transition of Barbados from the colonial, pre-modern to the modern era, including the Emancipation (1834), and the end of the apprenticeship system (1838)
- British Emancipator (1837-1840) – an anti-slavery newspaper that fought for the abolition of the system of apprenticeship, which was put into place after slavery was abolished in the British Colonies
- British Miner and General Newsman (1862-1867) – a journal devoted to working miners, which went through a number of titles including The Miner, The Workman’s Advocate and The Commonwealth
- Cobbett’s Weekly Political Register (1803-1836) – a famous and hugely information-rich vehicle for the ideas and opinions of the great nineteenth-century radical William Cobbett
- The Examiner (1808-1880) – a leading radical weekly, edited by Leigh Hunt, with contributors including William Hazlitt, John Keats and Percy Shelley
- Illustrated Sporting News and Theatrical and Musical Review (1862-1870) – a lively, visually rich newspaper covering a wide range of sports and theatrical events, with many fine illustrations
- Royal Gazette of Jamaica (1779-1840) – a West Indies newspaper notorious for its slavery advertisements
- Lady’s Newspaper and Pictorial Times (1847-1863) – one of the earliest newspapers produced for an exclusively female audience
- Morning Herald (1800-1869) – founded in 1780, a national daily that for a number of years rivalled The Times in importance
- Poor Man’s Guardian (1831-1835) – the most successful and influential of the radical unstamped (and thus illegal) newspapers of the early 1830s
- Sun (1801-1871) – a daily evening national newspaper, founded in 1792, originally with pro-government and anti-French revolutionary stance, before changing to advocate liberal and free trade principles
By providing free access to key areas of this unparalleled resource, Findmypast and the British Library are offering the public unique opportunities to uncover the stories behind historical events both great and small, as they happened; transforming their understanding of both the past and the present. This detail-rich archive sees the lives of ordinary people played out in print. Readers can discover contemporary reports on the struggles of the poor and working class, the daily lives of England’s mining communities, the evils of slavery, the campaign to end them and much more.
As well as providing free access, their use of Optical Character Recognition (OCR) and machine learning also means exploring these unique resources is easier than ever. You can search billions of lines of printed text by name, date, keyword or phrase, all from the comfort of your own home.
Findmypast Newsletter Friday 13 August 2021




